Recently there have been a number of phishing attacks targeting us and our customers. Our customer service team are dealing with high volumes of calls regarding the issue.
The email did NOT come from us, and is a form of scam. Please do NOT click on any of the links in the email. We take the security of customers and systems very seriously and to the best of our knowledge there has not been any breach of security.
Our senior staff are working with partners in the industry to get the malicious websites taken offline as quickly as possible.
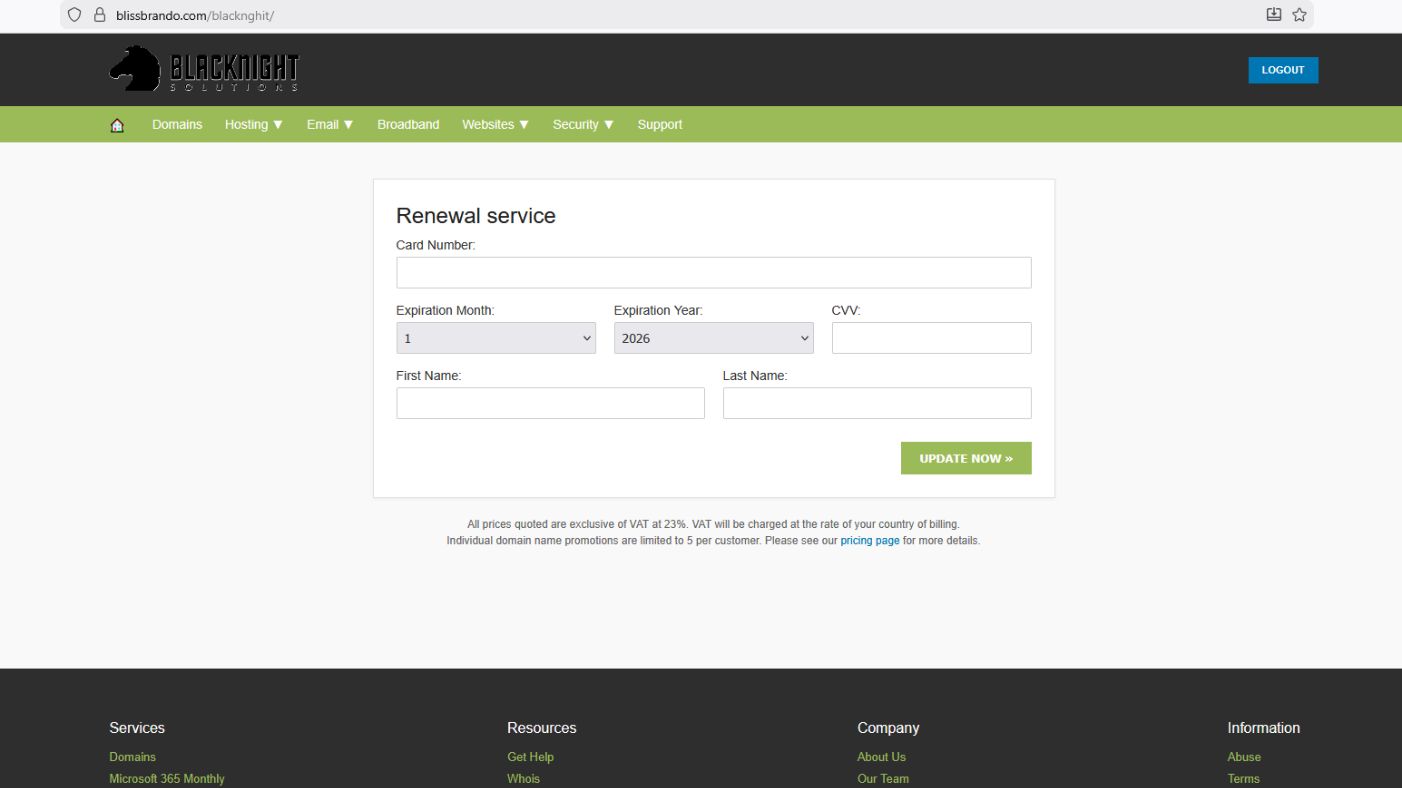
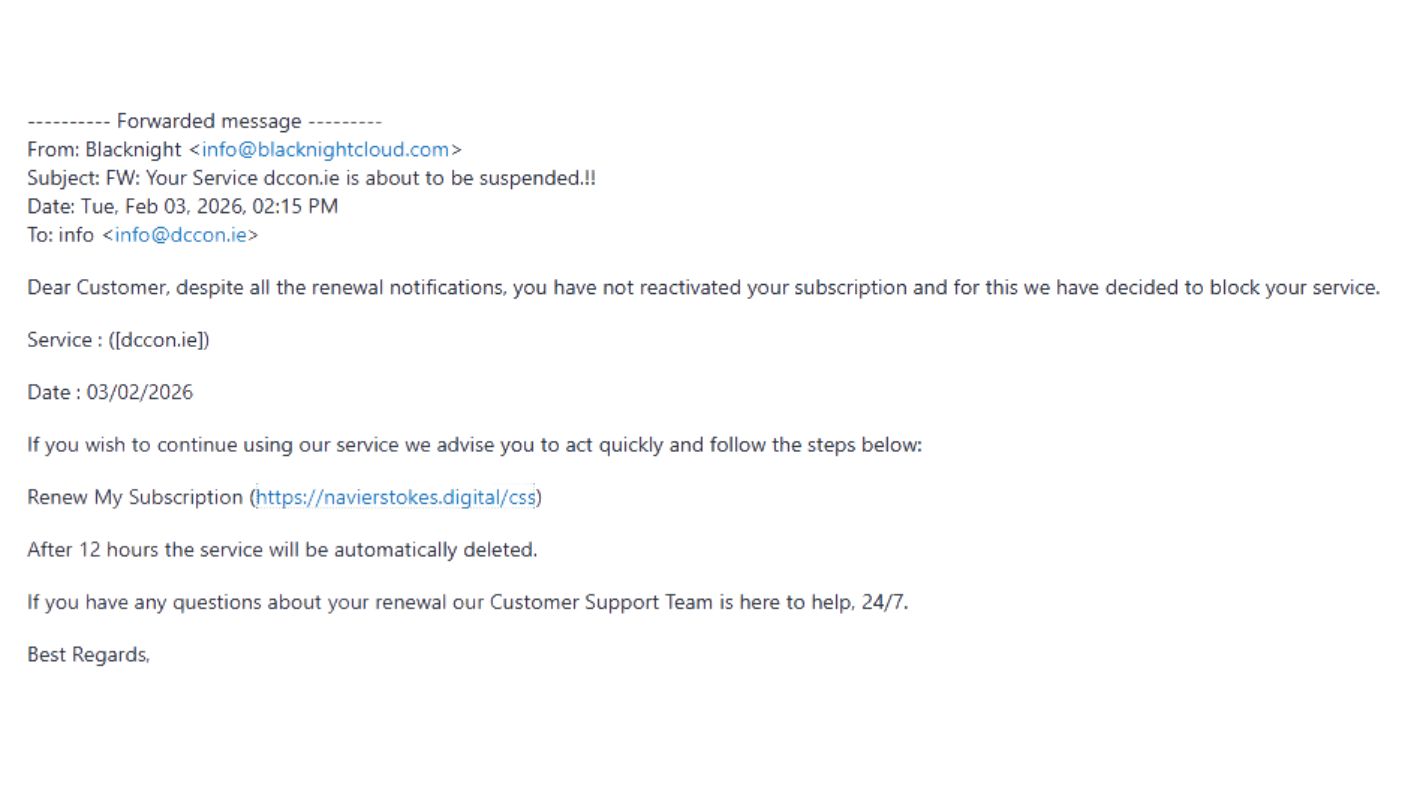
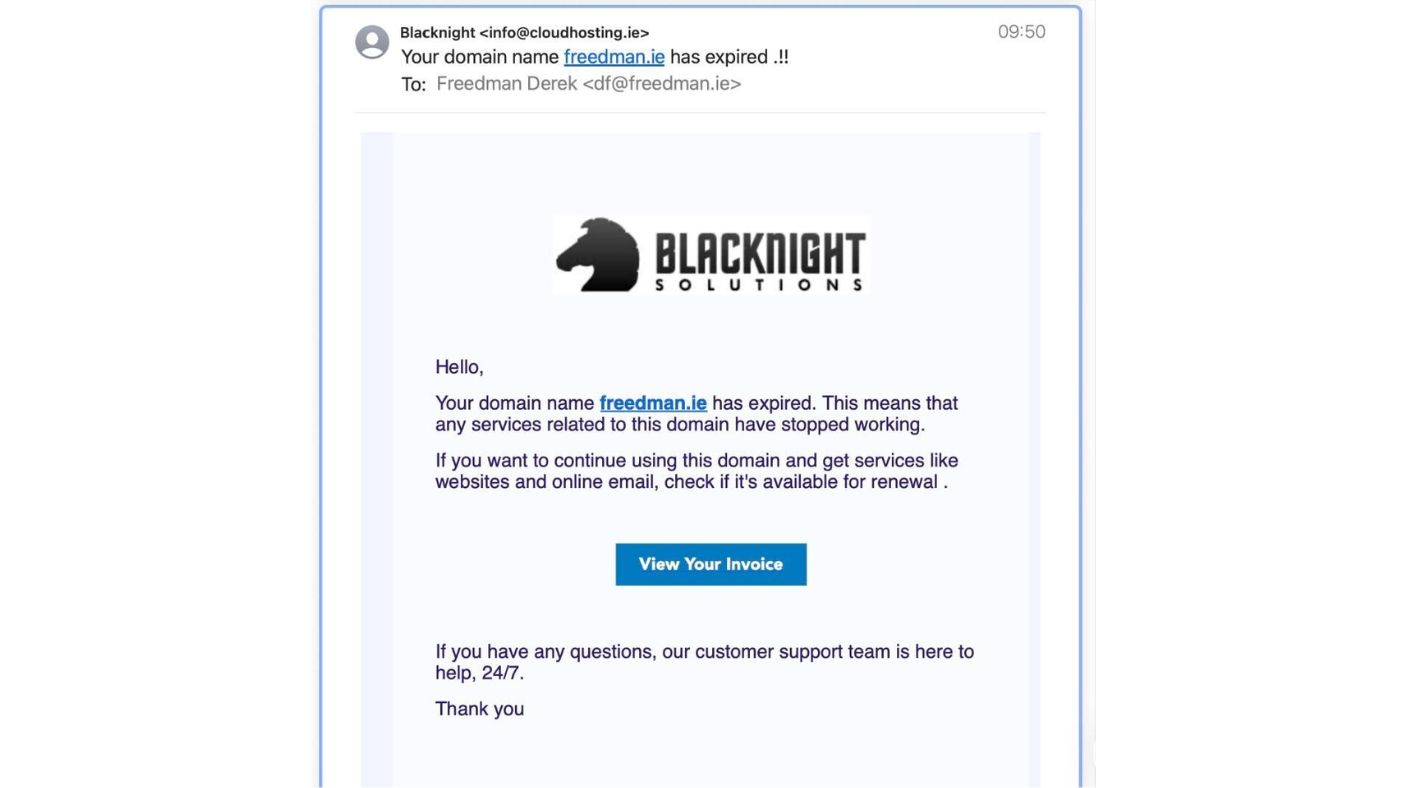
Below are some examples of a phishing email and a fake page that the link sends users to.
A few things to watch out for with these emails:
- Bad grammar is usually a frequent giveaway. Legitimate companies take care to present their corporate communications in a way that reflects well. Sloppy English can be a sign of a scam.
- Scare tactics. Phishing emails use threatening language like ‘suspension’, ‘no longer possible to renew’ and ‘permanently deleted’. If you are surprised to be told that your service has expired, stop and think. Wouldn’t we have warned you in advance?
- Look carefully at the link you are being asked to click. The linked text may look like a normal blacknight.com address, but the actual link it points to may be different. Does a different link address appear in the status bar at the bottom of the window when you put your mouse over the linked text? Don’t click it.
- If you have clicked the link, look at the address bar at the top of the browser window. Look at the hostname (or domain name) part of the address. This is the part after ‘https://’ and before the next ‘/’. This should contain only blacknight.com, or www.blacknight.com, or cp.blacknight.com. or cp.blacknighthosting.com It should not contain any other words. If it says something else, it is a fake.
- You should also note that the proper Blacknight login page includes a scam warning which is absent from the fake page.
- Blacknight sites use Digital Certificates with Extended Validation (EV). This means that the connection is secure, and also that the domain name has been independently verified as belonging to Blacknight. If you click the padlock icon in the address bar, you should see that the certificate has been issued to “*.blacknight.com” or “*.blacknighthosting.com” – and nothing else. If you don’t see this information, it’s not Blacknight.
We strongly advise customers to set up Two-Step Authentication on their Blacknight accounts, if they have not already done so.








Is this email below an April Fool?
Dear customer service,
Please note that there has been a mistake during the automatic renewal of your services (hosting, domains, e-mail …).
To resolve this issue, please check your bank information.We invite you to manually fill out the payment form for your
services according to the instructions in the link below :
https://cp.blacknight.com/update
We will deduct 1.19 EUR only to validate your credit card.
If your status is not settled within 24 hours, it is regrettable that we will close your account in accordance with your terms and conditions.
We thank you for your confidence in Blacknight Internet Solutions Ltd and remain at your disposal.
Regards,
Blacknight Solutions
——————————————————————————————————————-
Hosting, Colocation, Dedicated servers, Domains
IP Transit Services
IRL: 0818 929 929 / 059 9183072
US: 213-233-1612
UK: 0844 4849361
Intl. +353 59 9183072
Máirín
That email was another version of the scam targeting our clients.
Michele
Hi I had one of the April 1st emails, but it was sent from help@blacknight.com which is one of your domain names is it not?
I would like to forward it to you so that you can investigate, can you tell me what email to forward it to please.
Marrianne
Marrianne
The displayed “from” could look like it was from us, but the *real* sender isn’t. Either way if you want to send any reports to abuse@blacknight.com it’d be appreciated.
Thanks
Michele
Is there no way that Blacknight can stop these from getting through their servers? I am now getting 4 or 5 of these every day, but I don’t want to train my email system to treat them as junk in case I block genuine blacknight emails
Brigid
We block the emails as soon as we are aware of them ie. once we have reports of any new ones.
They aren’t being sent by us and are not using any of our domain names to send the email so blocking them shouldn’t impact genuine emails from us.
Michele
Strange thing is that Esat email is being migrated to Blacknight. I also thought that was a scam, so I phoned Blacknight and they confirmed that it was genuine.
Walter
There’s more information about it here:
https://blacknight.blog/blacknight-is-taking-over-the-iol-esat-oceanfree-email-services.html
Thanks
Michele
I was led to believe that there was no change in my email and that I didn’t need to do anything,
however, from today i have been unable to receive any emails to my present address,
Why is this??
Jim Ryan
Jim
You would have received several emails from BT about the move. Unless you opted in to move to ourselves BT will assume that you no longer want the service.
If you contact our helpdesk we can try to assist you.
Michele
The link that my email pointed to was :
http://cp.blacknight.com-updateaccount.lasermaxx-aventure.com/ie/
Is this genuine???
No, that is an example of a scam URL. The secret is to look at the part after the first ‘://’ and before the next ‘/’. This is the hostname. The correct blacknight login has the hostname cp.blacknight.com in that space and nothing else. You can see that the above link is a fake because the hostname is cp.blacknight.com-updateaccount.lasermaxx-aventure.com.
I’m seeing a rise in phishing e-mails generally. You’d think they drop off as people are more able to spot dodgy e-mails, but apparently not.
I recived every day on my business email and my client business emails scam like this not only from blacknight but as well from other institutions like BOI etc. The best way to protect your self is using email which is not public on your website or other websites, then scammers can’t track your email and can’t send you this emails.