
The latest ransomware exploit to create havoc on computers around the world shows the importance of businesses and home users keeping their computers updated with the latest security updates.
WannaCry, which Interpol estimates to have affected over 200,000 computers in 150 countries, is the latest high-profile ransomware cyberattack. And as quickly as it started it slowed when a 22-year-old cybersecurity researcher discovered a kill switch that was activated when a certain domain name in the code was registered.
Ransomware typically blocks access to a computer by encrypting all files with a very strong encryption, demanding a “ransom” to unlock it. A request for the ransom to be paid with Bitcoins, which are very hard to track to their destination, is the usual method. In this case the attacker demanded $300 in Bitcoins to unlock the files. The chances of recovering data are minimal without paying the ransom, but many security experts suggest paying the ransom only encourages future exploits. Further, it can’t be guaranteed that once the ransom is paid your files will be unlocked.
In Australia, the Telstra cybersecurity report 2017 found approximately 60% of Australian organisations reported experiencing at least one ransomware incident in the previous 12 months. Of the Australian organisations surveyed, 42% reported paying a ransom to cyber criminals. Nearly one out of every 3 who experienced a ransomware incident and paid the ransom did not recover their files. Further afield in Asia, 40% of organisations who paid the ransom did not recover their files.
It’s not just home users that have been impacted. The latest ransomware attack has had a huge impact on organisations still running Windows XP such as Britain’s NHS and Germany’s state railway Deutsche Bahn.
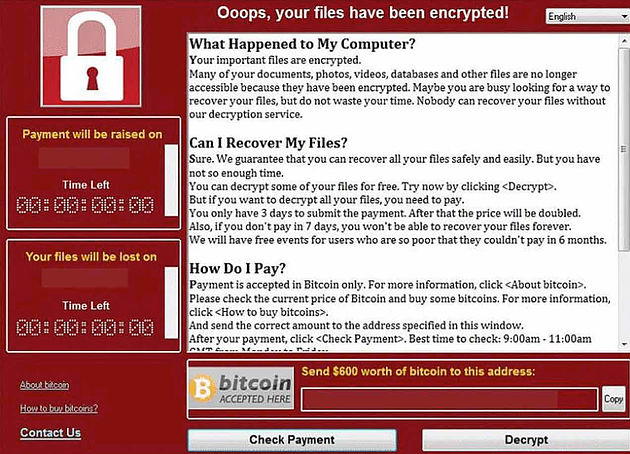
Microsoft released a security patch on 14 March to patch this vulnerability. This current attack has only impacted on Windows computers that haven’t been updated with this update, or those running Windows XP, Windows 8 and Windows Server 2003. The former has been unsupported since April 2014 but in recognition of the severity of WannaCry Microsoft has now issued a patch for these. But running unsupported software causes problems even greater than leaving software unprotected through lack of updates.
The WannaCry vulnerability is an exploit stored by the CIA and released via WikiLeaks, and now stolen from the NSA affecting customers around the world.
Microsoft has been scathing of the situation. Writing on the Microsoft blog Brad Smith, Microsoft’s President and Chief Legal Officer wrote in part:
“Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage. An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen. And this most recent attack represents a completely unintended but disconcerting link between the two most serious forms of cybersecurity threats in the world today – nation-state action and organized criminal action.
“The governments of the world should treat this attack as a wake-up call. They need to take a different approach and adhere in cyberspace to the same rules applied to weapons in the physical world. We need governments to consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits. This is one reason we called in February for a new ‘Digital Geneva Convention’ to govern these issues, including a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them. And it’s why we’ve pledged our support for defending every customer everywhere in the face of cyberattacks, regardless of their nationality. This weekend, whether it’s in London, New York, Moscow, Delhi, Sao Paulo, or Beijing, we’re putting this principle into action and working with customers around the world.”
So what to do if your computer or network has been infected? If you’ve kept recent backups, reinstalling the operating system and then files is the simplest and cheapest method, although it might take time. At the moment, without backups, your options are limited.
To avoid being exploited by ransomware exploits such as WannaCry, internet users and systems administrators should ensure:
- All systems are updated and all software including security software is up to date as well as automatic updates turned on.
- The latest operating system, or at least a very recent supported version, is installed.
- Ensure all files are regularly backed up to both the cloud and an external hard drive – for businesses, ensure at least three copies of the most valuable data are stored, two on different external media and one copy offsite, backups are completed successfully and are protected from being overwritten and systems are tested regularly. However any backup connected to an affected computer is likely to also be encrypted by the ransomware.
- Don’t open any suspicious files, files in emails from unknown recipients or click on suspicious or unknown links.
At Blacknight we have ensured all our Corporate systems are patched and protected.
For your security, Blacknight offers a number of backup services including laptop, desktop and server backups, file and disk backups, local and cloud storage and recovery services. Our Acronis AnyData Engine backs up to local storage on your premises for quick restore and to secure Acronis Cloud data centres for disaster recovery. All hosted in the European Union.
If you believe your system may not be patched to protect against WannaCry, the most important step involves patching the Microsoft vulnerability (MS17-010), which you can download from:
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
A patch released in the last few days for legacy platforms such as Windows XP and Windows 8 is available here:
https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks
For IT managers, in instances where it is not possible to install the patch, managing the vulnerability becomes the key. One way of doing this would be to disable the SMBv1 (Server Message Block) protocol:
https://support.microsoft.com/en-us/help/2696547 and/or block SMBv1 ports on network devices [UDP 137, 138 and TCP 139, 445].
For more information, the UK’s National Cyber Security Centre has published a “Ransomware: Latest NCSC Guidance”
https://www.ncsc.gov.uk/guidance/ransomware-latest-ncsc-guidance
Interpol has also published a No More Ransom page that provides advice on unlocking a computer or mobile phone at:
https://www.nomoreransom.org/





