WordPress Security is a big thing for us as we host a LOT of WordPress sites. Not having an up to date install can mean things can get exploited and hacked. This could result in spam emails being sent. Spam content put into your site and you may even see your site suffer in rankings on the likes of Google.
So I revisited an old personal WordPress install of mine the other day. You know the type of blog you almost forget you have. You don’t update and it just sits there for a while doing absolutely nothing?
I went about upgrading the plugins and core of WordPress and I went and I added in the WordFence plugin (which I’ve written about recently) to provide me with notifications about out of date plugins / suspicious files and so on.
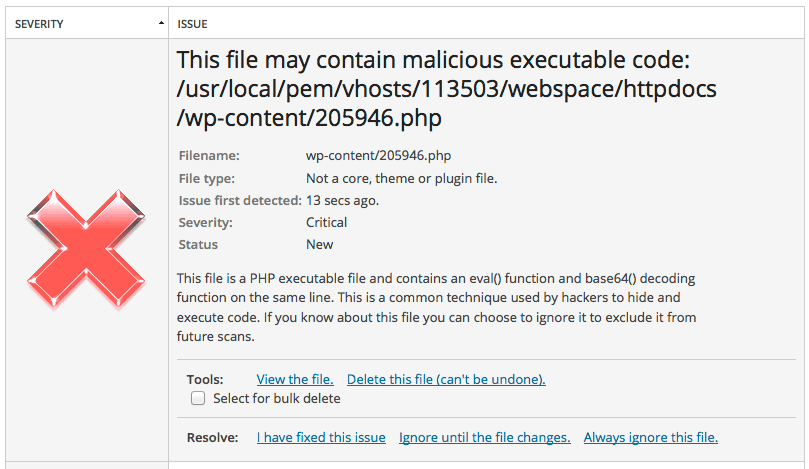
When I turned on WordFence and ran a scan it came across 17 suspicious files similar to the below.
Investigating the files I can view the content of the file clicking on the “View the file.” link. This shows me a lot of encoding stuff going on so it’s pretty safe to assume these are not nice files. You could go and reverse engineer the file if you really wanted but I didn’t bother.
With the correct permissions set, WordFence can go ahead and delete the files for me. Ticking the “Select for bulk delete” will let you delete a batch of the files if you wish speeding up the process. I wanted to confirm the contents of each of the files so went through them one by one.
There were php files located in the /wp-content/uploads/ folder.
PHP files in /wp-content/uploads/ hmm that shouldn’t be. The uploads folder is for files you upload right? Generally image or video files .. PDFs. We shouldn’t really have any PHP files in there.
If an out of date plugin, theme or WordPress core files are to blame chances are PHP files were uploaded to this folder first and this then infected the rest of the site. (Not always but a lot of the time)
What can we do about that though? Why not disable the execution of PHP in these folders?
Create a .htaccess file and include the following in it and upload it to your /wp-content/uploads/ folder. This folder and all subfolders will take on the do not allow access to these PHP files from a web browser.
<Files *.php>
deny from all
</Files>
Now I can’t say 100% that this won’t break some obscure plugin and well if it does just remove the .htaccess file and your plugin should start working again.
What’s a .htaccess file you may ask and how do I create one?
If you’re asking this then the easiest way is to open up notepad (on a windows machine) and create a normal text file put the above code into it.
Upload this text file to your /wp-content/uploads/ folder and then rename it to .htaccess
To test out if it’s working simply put
<?php
phpinfo();
into a test php file lets call it test.php and upload it to your /wp-content/uploads/ folder and you should receive the following warning if you try to access it directly in a web browser ( http://your domain/wp-content/uploads/test.php )
Forbidden
You don’t have permission to access /wp-content/uploads/test.php on this server.
Any other nice tips you have for securing your WordPress install even further? Let us know.
3 Comments
Comments are closed.






RT @blacknight: Hardening your WordPress Security: http://t.co/yvMxBJc06g
RT @blacknight: Hardening your WordPress Security: http://t.co/yvMxBJc06g
RT @blacknight: Hardening your WordPress Security: http://t.co/yvMxBJc06g